
Supporting Veteran owned organizations is our first priority.
Security
Aligned
Business Readiness Solutions
ISA Cyber Threat Infrastructure specializes in Cybersecurity Governance, Risk, and Compliance (GRC), vCISO/CIO/COO, and critical infrastructure business program management solutions for Veteran-owned organizations and businesses across a wide range of sectors. We support business operations, cybersecurity initiatives, and digital transformation efforts through practical, risk-driven leadership and execution.
Core
Services
Our projects are chosen based on resource requirements, scope, and timeline. Our project teams consist of Veteran and civilian subject matter experts in various aspects of cybersecurity-business-alignment, healthcare and financial information systems, governance, risk, compliance, engineering, threat intelligence, threat hunting, penetration testing, incident response, and forensics. In addition to security services our information system specialists provide a number of critical infrastructure business program management solutions.
Complementing our core team, we engage Veteran volunteers and student interns who actively support a range of business, cybersecurity, and information systems functions, contributing to the successful execution of select initiatives and ongoing operations. Let us know how we can help you build a strong and resilient cybersecurity and information assurance posture, while also supporting your broader digital transformation goals in healthcare and financial information systems.
CYBERSECURITY GOVERNANCE
Cybersecurity governance is the framework that provides the structure for managing and controlling cybersecurity-related processes within an organization.
RISK MANAGEMENT
Our risk management services help businesses identify, assess, and prioritize cybersecurity risks to minimize their impact.
COMPLIANCE SOLUTIONS
We offer comprehensive compliance solutions to ensure that businesses adhere to industry regulations and standards, safeguarding their digital assets.
FRACTIONAL vCISO/CIO
Strong cybersecurity begins with a top down strategy. Our security experts will work with your security teams to being your cybersecurity program into business alignment.
SECURITY AUDITS
Our security audits help businesses evaluate the effectiveness of their cybersecurity measures, identifying vulnerabilities and recommending enhancements.
SECURITY AWARENESS
We provide specialized training and awareness programs to educate employees about cybersecurity best practices, empowering them to contribute to a secure work environment.
_edited.jpg)
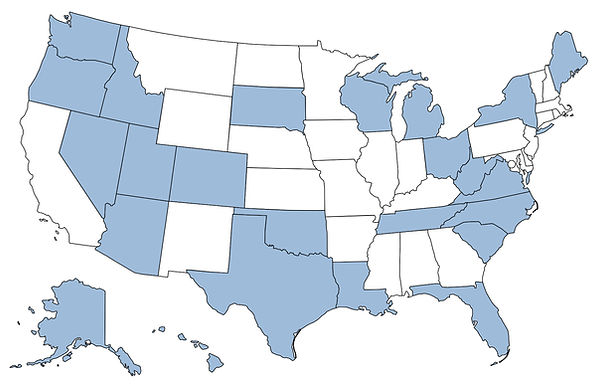
ISA Cyber Threat Infrastructure maintains an expanding presence across the states, where multiple consultants, veteran volunteers, and student interns are actively engaged in a range of customer programs and projects. These efforts span key service areas, including cybersecurity, governance, risk, and compliance (GRC), as well as the implementation, integration, and ongoing support of healthcare and financial business systems and projects. Our distributed structure enables us to deliver tailored solutions that meet the complex regulatory, operational, and security needs of small and mid-sized Veteran-owned and privately held organizations. As demand grows, so does our commitment to recruiting experienced professionals and developing emerging talent, ensuring we continue to deliver high-quality outcomes across a geographically diverse customer base. The map above illustrates the reach of our teams and the breadth of our active engagements nationwide.

Governance, Risk, and Compliance
In today’s dynamic digital environment, effective Governance, Risk, Compliance (GRC), and Privacy strategies are essential to ensure both operational resilience and regulatory compliance. At ISA Cyber Threat Infrastructure, we take a holistic, enterprise-wide approach to designing and executing GRC frameworks that not only mitigate risks but also align with your broader business goals.
Our project team integrates risk management controls into IT services processes, simplifying the consolidation of compliance requirements across multiple frameworks such as ISO 27001, NIST CSF, SOC 2, HIPAA, and PCI-DSS. By developing clear, actionable objectives and streamlining control models, we help reduce the duplication of effort across IT and business teams while focusing on the delivery of secure, measurable, and high-quality IT services.
As organizations face increasing regulatory demands and complex technological landscapes, a well-established and proactive GRC program is more crucial than ever. We prioritize governance, data integrity, and assurance, enabling organizations to stay ahead of compliance challenges and prepare for future business growth. Our approach includes the development and implementation of robust policies, procedures, and controls that not only align IT goals with business objectives but also ensure that business processes are secure and compliant.
At ISACTI, we recognize that GRC is about more than just managing risks related to emerging technologies or evaluating IT performance. It’s about embedding governance into the organization’s DNA, creating a security-driven culture, and helping you develop a sustainable, resilient environment that adds long-term value by addressing both current and future risks.

Fractional CISO, CIO, and COO
Hiring a full time Chief Information Security Officer (CISO), Chief Information Officer (CIO), or Chief Operating Officer (COO) can be a significant financial commitment, especially for organizations with evolving business and technology needs. Many organizations do not require dedicated, in house executives for each role but still need trusted leadership and strategic guidance to build, secure, and operate effective information security, technology, and operational programs. Fractional executive services provide executive level expertise without the full time overhead.
At ISACTI, we offer flexible, on demand vCISO, vCIO, and vCOO services that allow you to access experienced executive leadership when needed. Our fractional executives help you navigate cybersecurity, technology strategy, and operational complexity, from regulatory compliance and risk management to IT modernization and operational alignment, while balancing business needs with budgetary constraints. This enables you to focus on growth with confidence that critical functions are in expert hands.
Our fractional services are designed to assist in key areas including security operations, data protection, infrastructure and application management, governance and compliance, and risk mitigation. By leveraging our network of subject matter experts, we provide tailored support to meet your unique needs, whether addressing urgent challenges, guiding existing leadership, or preparing internal leaders for future executive roles. Ultimately, we help organizations build resilience and maturity to manage both current and future risks effectively.

Risk Management
Effective risk management is a cornerstone of robust cybersecurity and information security practices. At ISACTI, we specialize in identifying, assessing, and mitigating cybersecurity risks that could jeopardize your organization's information assets, infrastructure, and operational continuity. We understand that risk management must be tailored to your organization’s specific needs, considering its size, industry, and technology environment. Our approach integrates cyber risk management across your entire organization, aligning with your business objectives and ensuring proactive measures are in place to manage both internal and external threats.
Cybersecurity risk is inherent in every business, and managing it requires a comprehensive, coordinated approach. We work alongside your team to develop a robust enterprise risk management (ERM) framework that not only evaluates technical vulnerabilities but also considers the broader business impact of potential cyber threats. Our services are designed to help you assess and manage risks from a variety of sources, including third-party vendors, regulatory compliance requirements, data privacy obligations, and the evolving threat landscape.
Our methodology includes conducting detailed cyber risk assessments that analyze the effectiveness of your security controls, data protection mechanisms, and incident response procedures. We focus on understanding how risks impact your business operations, technology infrastructure, and overall resilience. Whether it's improving your security posture through policy development, risk control implementation, or aligning with industry standards such as NIST CSF, ISO 27001, PCI-DSS, HIPAA, or SOC 2, we ensure your organization has the tools and processes in place to respond to and recover from potential incidents effectively.
At ISACTI, we recognize that cyber risks are not isolated but deeply intertwined with business risks. Our comprehensive approach empowers organizations to transition from reactive to proactive risk management. We help you establish a sustainable risk management culture that enables continuous improvement in your cybersecurity practices while ensuring compliance with relevant industry regulations.
By engaging with ISACTI, you gain access to a dedicated team of cybersecurity experts who will guide you through the complexities of identifying, mitigating, and managing cyber and information security risks. We work with you to develop an actionable, long-term strategy that strengthens your security posture and ensures your business remains resilient in an ever-changing threat landscape.
Security Audits and Assessments

At ISACTI, we excel in conducting comprehensive security risk assessments, focusing on both internal systems and third-party vendor environments. Our team of security audit experts helps you uncover vulnerabilities, identify gaps in your current security posture, and pinpoint areas where non-compliance may exist. By performing a detailed Cyber Security Audit, Compliance Audit, and Data Security Audit, we provide you with a clear, actionable understanding of your organization’s cybersecurity health.
Our audits assess the effectiveness of your existing security controls, data protection measures, and compliance with relevant regulations such as NIST, ISO 27001, HIPAA, PCI-DSS, SOC 2, and others. We evaluate both internal systems and third-party vendor relationships, ensuring that external risks, like vendor security, are fully understood and addressed. Third-party vendor assessments are crucial, as these relationships often present significant security risks, including data breaches, regulatory violations, and operational disruptions.
Following the completion of our audits, our GRC team provides a comprehensive risk report that outlines key findings, identifies compliance gaps, and prioritizes areas for remediation. This foundation allows us to collaborate with you in designing and implementing tailored security strategies that address these gaps and mitigate risk.
In addition to supporting your compliance efforts, our audits are also invaluable in investigating potential internal anomalies or suspected wrong-doing. Our findings can be used to strengthen your internal controls, implement corrective actions, and, if needed, serve as key evidence in legal proceedings or litigation. By identifying security weaknesses proactively, we help reduce the likelihood of future incidents, providing peace of mind and reinforcing your organization’s cybersecurity framework.
We ensure your organization’s cybersecurity resilience, helping you manage and mitigate risks from both internal systems and third-party vendor relationships. We provide the insights and tools necessary to build a stronger, more compliant, and secure business environment.

Compliance Assistance
We specialize in assisting veteran-owned and privately held organizations with navigating the complex landscape of cybersecurity compliance. Our team of experienced professionals helps identify vulnerabilities, assess real business risks, and streamline the compliance process by consolidating multiple regulatory frameworks into a single, unified approach. We help ensure that your organization meets essential compliance standards, such as SOC 1, SOC 2, PCI-DSS, HIPAA, GLBA, ISO 27001, CMMC, and more, while simplifying the process and reducing redundant efforts.
By focusing on common controls across these frameworks, we reduce the complexity and effort needed to maintain compliance across multiple standards. Our experts work with your team to establish security and governance programs tailored to your environment, ensuring alignment with both business objectives and regulatory requirements. We also support organizations in preparing for and recovering from cybersecurity incidents, providing strategic guidance to enhance your overall security posture.
With years of experience across various domains of information security, we help you align your technology stack, policies, procedures, network design, and incident response strategies with industry-leading standards. Our services are fully customizable, addressing every aspect of cybersecurity compliance—from risk management and disaster recovery to compliance audits and beyond. We are committed to simplifying the process for your team, enabling you to meet compliance obligations efficiently and with confidence.

Employee Awareness and Human Risk
We understand that employees are a key element of an organization’s overall security posture. As human error, action, or inaction contributes to more than 60% of cybersecurity breaches, equipping your workforce with the knowledge and skills to defend against threats is vital. In addition to being part of a healthy security program, comprehensive security awareness training is often required to meet industry regulations such as FISMA, PCI-DSS, HIPAA, Sarbanes-Oxley, CCPA, and GDPR.
Our team works with your organization to develop and implement effective cybersecurity awareness and education programs tailored to meet both regulatory compliance requirements and real-world threats. We leverage the expertise of our cybersecurity and information security team members and veteran volunteers, who bring invaluable experience to help identify and address employee weaknesses before cybercriminals can exploit them.
Beyond traditional security awareness, we’ve incorporated the growing field of Human Risk Management (HRM) into our programs. HRM recognizes that employees, rather than being seen solely as potential threats, can be a significant asset in strengthening security. With the right training and support, employees become key defenders of the organization. Our HRM-focused approach transforms your team into cybersecurity champions, better equipping them to resist manipulation tactics and reduce human risk.
Our customized programs empower employees to recognize, respond to, and mitigate security threats, making them an active part of your defense strategy. With ISACTI, your organization gains the critical security awareness necessary to reduce vulnerability and ensure the safety of both your data and your digital infrastructure.

Security Operations - VM - Incident Response
At ISACTI, we empower small Veteran-owned and private businesses to build resilient, risk-informed vulnerability management programs. Rather than relying on generic scanning routines, we guide organizations in developing real-world threat exposure management workflows—linking business impact, exploitability, and active threat intelligence to prioritize what truly matters. From initial asset discovery to ongoing vulnerability triage and remediation planning, our experts help implement a tailored, contextual approach aligned with frameworks like NIST CSF, CIS Controls, and EPSS-informed risk scoring. We also assist with creating remediation workflows that integrate into your existing operations, whether that's through IT ticketing, DevSecOps pipelines, or small-business-friendly automation platforms like Tines or n8n.
Beyond vulnerability management, ISACTI helps organizations grow their Security Operations Center (SOC) and Incident Response (IR) programs from reactive to mature and proactive. We support your team in developing detection playbooks, alert triage procedures, and incident escalation paths that are tightly integrated with business risk. Our services include building custom use case libraries based on your environment, helping deploy or optimize endpoint detection platforms, enhancing log visibility, and guiding tabletop exercises for real-world readiness. Whether your SOC is just starting or seeking to evolve, we help build repeatable processes, measurable metrics, and incident-handling capabilities that align with your company’s risk profile and resource level.
Program & Project Management - Health and Finance

We help healthcare and financial organizations design and implement information systems programs that drive operational excellence and regulatory compliance. Our experts work with clients to develop governance and management practices that align technology initiatives with business objectives, whether implementing a new EHR (Epic, Cerner), LIS, PACS, VNA, RIS, or modernizing core banking, loan origination, FIS, CRM, treasury management, or trading systems. From initial system discovery and requirements gathering, through vendor evaluation, integration planning, and security risk assessments, we guide organizations in building resilient, well-governed programs. We focus on workflow design and optimization to ensure new platforms support both operational needs and compliance frameworks like HIPAA, HITRUST, PCI-DSS, SOX ITGCs, NIST CSF, or ISO 27001. Our program managers bring together cross-functional teams to oversee every stage of implementation, from interface mapping and data migration to user training and go-live support, ensuring projects are delivered on time, within scope, and fully integrated into existing business and clinical workflows.
Frameworks
and Compliance


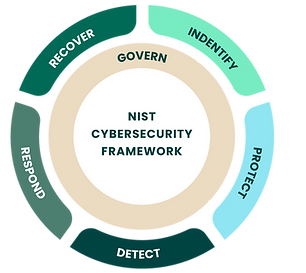
Regulatory compliance, standards, and frameworks in cybersecurity, such as COBIT, NIST CSF, ISO 27001, SOC1 and SOC 2, PCI-DSS, HIPAA, C2M2, and other standards, play a pivotal role in safeguarding sensitive data, ensuring privacy, and fortifying organizational resilience against cyber threats. These frameworks provide structured guidelines, best practices, and standards tailored to different industries and compliance needs, offering a roadmap for organizations to establish robust cybersecurity measures. Adherence to these frameworks not only mitigates risks but also fosters trust among stakeholders, enhances brand reputation, and facilitates regulatory compliance. However, navigating the complexities of multiple frameworks and ensuring compliance can be daunting for organizations. Our company specializes in providing tailored solutions and expert guidance to help clients decipher these intricate frameworks, implement effective cybersecurity measures, conduct thorough risk assessments, and achieve regulatory compliance seamlessly. Through our comprehensive approach, we empower clients to navigate the intricate landscape of cybersecurity regulations with confidence, enabling them to focus on their core business objectives while safeguarding their digital assets and reputation.
Below, are just some of the security standards and frameworks that our subject matter experts have experience implementing. Let us know if you have questions regarding these or others on our compliance and frameworks page.
NIST CSF: The NIST Cybersecurity Framework (CSF) is a comprehensive set of guidelines, best practices, and standards designed to help organizations manage and improve their cybersecurity posture. It provides a structured approach for organizations to assess and strengthen their cybersecurity capabilities across five core functions: Identify, Protect, Detect, Respond, and Recover. By utilizing the CSF, organizations can better understand their current cybersecurity risks, establish effective risk management processes, and implement appropriate security controls to mitigate threats. Its importance lies in its flexibility, adaptability to various industries, and alignment with both existing cybersecurity standards and regulatory requirements. Additionally, it fosters a common language for discussing cybersecurity risks and encourages collaboration between stakeholders, ultimately enhancing the overall security resilience of organizations.
ISO 27001/27002: ISO 27001 is an internationally recognized standard that provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. It outlines requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). This standard helps organizations identify and address security risks systematically through risk assessments and the implementation of appropriate controls. By adhering to ISO 27001, organizations can demonstrate their commitment to protecting valuable information assets, enhancing trust with stakeholders, complying with legal and regulatory requirements, and ultimately improving their overall cybersecurity posture.
SOC 1 and SOC 2: SOC 1 and SOC 2 are two types of reports issued by independent auditors to assess the controls and processes related to the security, availability, processing integrity, confidentiality, and privacy of data within service organizations. SOC 1 reports focus on controls relevant to financial reporting, particularly for outsourced services that could impact the financial statements of a client organization. This is especially important for companies subject to regulations such as Sarbanes-Oxley (SOX). On the other hand, SOC 2 reports evaluate controls relevant to security, availability, processing integrity, confidentiality, and privacy, with a focus on technology and cloud computing services. These reports help service organizations demonstrate their commitment to meeting stringent security and privacy requirements, providing assurance to clients and stakeholders about the effectiveness of their internal controls and risk management practices. Both SOC 1 and SOC 2 reports are valuable tools for evaluating the security and reliability of service providers, helping organizations make informed decisions about their partnerships and ensuring the protection of sensitive data.
More about regulatory compliance and security frameworks here.
About
ISA Cyber Threat Infrastructure
.png)
ISA Cyber Threat Infrastructure began its journey in 1998 as the Veteran Support Center, originally established as a Managed Service Provider (MSP) and IT training center with a dedicated focus on Veteran-owned businesses. Leveraging subject matter expertise rooted in military service and applied across IT, information systems, and security, the organization provided core services to small and medium-sized businesses (SMBs): IT and security support to strengthen technical operations and safeguard data, and workforce development through hands-on training. The goal was to help SMBs, often lacking in-house technical resources, gain reliable IT infrastructure, basic network security protections, and the skills to operate and grow their businesses. What began as a mission to serve Veteran entrepreneurs steadily expanded into a broader effort to support SMBs across multiple industries.
In 2019, we expanded our mission to provide specialized project services in two critical areas: cybersecurity and business enablement. On the cybersecurity and GRC side, we deliver risk management, compliance frameworks, and fractional vCISO/CIO leadership to strengthen posture and reduce organizational risk. On the business side, we support financial and healthcare organizations with business case development, enterprise project management, and the implementation, integration, and governance of complex information systems. Together, these services reflect our evolution into a comprehensive project and program partner for security, governance, and enterprise success
Today, ISA Cyber Threat Infrastructure stands as a committed partner in securing and managing your business endeavors. We bring together a team of seasoned professionals with extensive expertise in business program oversight, business operations, project management, cybersecurity, and regulatory compliance. Our Veteran volunteers and student interns also contribute to our projects, providing fresh perspectives and supporting our mission-driven work.
Guided by experienced team managers, we ensure every project is delivered with a focus on quality and effectiveness. We approach each engagement with a deep understanding of the unique cybersecurity challenges organizations face today, offering customized solutions that empower businesses to navigate the complexities of their security landscape with confidence.
As a focused and mission-driven organization, we carefully select the projects we take on to ensure we can fully meet your needs, stay aligned with your timeline, and provide the dedicated attention your organization deserves. We commit to a number of pro-bono projects each year, staying true to our roots of service. Your leadership team will collaborate closely with our experienced project managers and subject matter experts, each specializing in different facets of industry and compliance.
To find out if your organization aligns with our purpose, reach out to us using the contact form below or send us an email. Let us know about your company, the security challenges you're facing, and how we can help strengthen your business.

Get In Touch
We offer a number of pro-bono projects throughout the year for Veteran owned businesses. Inquire today.
For staff, Veteran, or intern employment verification and references please email HRteam@isacti.org. Be sure to include the employee or intern name, as well as your reference document and questions. We will try to reply within 2 business days.
We have moved.
As of 12/23 we are no longer located in the Technology Blvd office.
Tel: 512.883.1095
10900 Research Blvd.
Austin, TX 78759


